What is TREZOR?
TREZOR is a single purpose device which allows you to make secure Bitcoin transactions. With TREZOR, transactions are completely safe even when initiated on a compromised or vulnerable computer. Because the use of TREZOR is very easy and intuitive we believe it will help Bitcoin adoption among people not familiar with the security issues.
How does TREZOR work?
The Bitcoin protocol works by sending signed notes of payment across the Internet. These messages (which are referred to as Transactions) are signed using a special algorithm. In order to sign a Bitcoin transaction, you need to have a special key or password. TREZOR holds that key. Since TREZOR’s job is to help you securely sign Transaction messages, you can think of your TREZOR as a modern day stamp.
TREZOR is better than an ordinary mechanical stamping mechanism, however. Each TREZOR has a PIN code. If your TREZOR gets stolen, thieves cannot misuse it to steal your money. Due to TREZOR’s clever design, even if the computer with which you use your TREZOR is hacked, the hackers will never know your PIN.
In contrast to the various pieces of software and web services that allow you to store your Bitcoins TREZOR is secure. Software and web-based solutions keep your Bitcoin signing keys either on your computer or worse, on the Internet! When you use such a service, hackers can easily steal your Bitcoins by hacking your computers or hacking the servers of the services that you use.
Which operating systems and devices support TREZOR?
There is full support for Windows (version 7 and higher), OS X (version 10.8 and higher) and Linux. You can also use your TREZOR with Android devices which have USB On-The-Go (aka USB Host).
Which wallets are compatible with TREZOR hardware?
The list of wallets that can be used with TREZOR device is constantly growing. These inlude TREZOR Wallet, Mycelium, and Multibit HD. To see the full list, please check out our TREZOR Apps.
Which wallets are compatible with TREZOR recovery seed?
In case your TREZOR is not available you can still recover your bitcoins using your recovery seed and a compatible wallet like Mycelium, Wallet32 or Electrum. Check out our TREZOR Apps for the full list of wallets compatible with the recovery seed.
Which wallets or services can import TREZOR account public keys (xpub)?
There is a growing number of wallets and online services, which you can use to watch your TREZOR account balances or receive bitcoins directly into your TREZOR without connecting the device. These apps cannot spend your coins but can check balances online or generate new receiving addresses for you.
To find out more about these apps, please look for wallets and services with “Watch-only mode” feature icon in TREZOR Apps
Which coins are currently supported?
At this moment it is Bitcoin, Ethereum, Ethereum Classic, ZCash, Litecoin, Namecoin, Dogecoin, Dash and Testnet. Please check up to date list at our repository.
Please check the TREZOR Apps for detailed information about the wallets supporting TREZOR
How is TREZOR different from …
an ordinary Web Wallet?
When you store your Bitcoins in a traditional web wallet you put your Bitcoins at risk of being stolen, lost, or confiscated. Here is a list of ways people have lost their Bitcoins through use of a traditional web wallet:
- User’s computer is hacked and web wallet password is stolen
- Web wallet server gets hacked and bitcoins are stolen
- Web wallet company goes bankrupt
- FBI or other enforcement agency confiscates coins
- Web wallet provider points to ToS violation and takes coins
- Owners of web wallet company run away with coins
- Bug in web wallet software leads to loss of coins
- Your computer or cell phone is stolen while you are logged in and thieves then steal your coins
If you keep your Bitcoins in a TREZOR, none of these things can happen.
a desktop Bitcoin client?
If you keep your Bitcoins on your computer, when your computer is hacked or stolen your Bitcoins can be stolen.
your mobile phone?
There are a number of programs that will allow you to send bitcoins from your mobile phones. Some are simply mobile interfaces to web wallets and suffer from the same flaws. Some are the same as desktop clients and can suffer from malware or theft.
a USB flash drive?
A USB flash drive is just storage for private keys. It means that when you want to make a transaction, you must attach your drive to the computer and let your bitcoin software read the keys from the device. At this point, your private keys are accessible to viruses and malware, just as to any other software on your desktop computer.
On the contrary, TREZOR is a single-purpose computer, which stores your private keys and actively signs transactions without sending your private keys to the computer. When you want to make a bitcoin transaction, your bitcoin software just sends a transaction template to the TREZOR device and asks for a digital signature. TREZOR shows the requested amount and target address on its display. You will then confirm the transaction by pressing the hardware button. TREZOR will sign transaction internally and send the digital signature back to the computer, without leaking your private keys. Thanks to this, you can use TREZOR even on a vulnerable or hacked computer.
an encrypted wallet?
Even using a strong password doesn’t prevent viruses to silently sit on your computer and wait until you want to transfer coins out of your wallet. This is a vulnerable point because a virus has access to the wallet file and can read your passphrase from your keyboard.
On the contrary, TREZOR never sends private keys to the computer, because when you want to send some coins out of your wallet, TREZOR asks bitcoin software for payment details, signs the transaction internally and then sends back just a digital signature of the transaction. There’s no point where malware on your computer could access the private keys or send away your coins without your permission.
Yubikey?
There is a significant difference between the two. The Yubikey is a device which helps the service to verify that it is actually you who is signing the transaction. However, it does not protect you against signing a different transaction than you intend to.
a paper backup of my keys?
A paper backup is a quite safe method to protect bitcoins, but you still need to load private keys from paper using a trusted computer to send your coins to somebody else.
Software design & security
What are a recovery seed, a PIN and encryption passphrase and the difference between them?
Recovery seed is a mnemonic code made of 12, 18 or 24 words depending on your choice. This seed is generated the first time you run TREZOR and will help you recovering it’s contents (private keys, bitcoin balance, and transaction history) into a new device if you lose your TREZOR.
PIN is a number that you set when you first run TREZOR. It protects TREZOR against being used by unauthorized persons. We have invented a secure way of entering the PIN so it can’t be keylogged and misused.
Encryption passphrase can be set on top of the PIN. This protects the device in case of a seizure. It’s using military-grade encryption of the seed on TREZOR storage, so even torturing the device in a laboratory won’t leak your private keys.
A combination of these security mechanisms makes your bitcoin ownership with TREZOR absolutely safe.
Is it safe to enter the PIN on my computer and not on the TREZOR itself?
TREZOR doesn’t have a keyboard but even if you enter the PIN on the computer directly, you’re perfectly safe. TREZOR’s PIN mechanism is protected against key-loggers, so using it even in internet cafes means no risk for you.
Why should I trust TREZOR with my private keys?
Because the entire software design of TREZOR is open-source. You can verify the product by yourself or find some other professional you trust to do so.
How can a seed made of several simple words be more secure than a strong password with caps or numerical signs?
This picture explains it all:
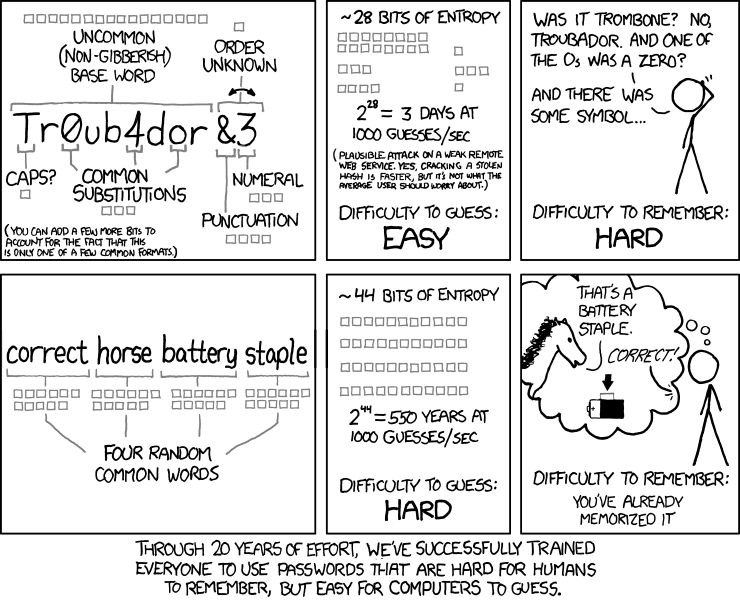
Comic by XKCD: Randall Munroe, licensed under Creative Commons Attribution-NonCommercial 2.5 License.
Why should I do a paper backup of my seed?
We think paper backups are the easiest and safest way of storing such information for a common computer user. Computer backups, on the contrary, are vulnerable to hardware damage and subject to frequent hacker attacks.
If somebody steals my TREZOR, they’ll just empty out my wallet before I have the chance to restore anyway. Right?
Not at all. All operations on TREZOR require the user to enter a PIN. The attacker would have to guess your PIN which is very difficult because with each badly entered PIN the time for entering it anew increases exponentially. For example, the delay between 19th and 20th PIN entering is 35 hours. Unplugging and plugging the device won’t help. The thief would have to sit his life off entering the PINs. Meanwhile, you have enough time to move your funds into a new device or wallet from the paper backup.
You can also hide your wallet behind passphrase which can be set on top of the PIN.
How to buy a TREZOR?
Click on the link below:
